Data Security in Flutter: Best Practices for 2024

In today’s rapidly evolving technological landscape, there is an increasing need for robust data security. With the emergence of Flutter, an agile framework for building cross-platform applications, it’s imperative to stay ahead of potential security threats. In this article, we’ll dive into the top best practices for ensuring data security in your Flutter applications in the year 2023.
 Code Obfuscation
Code Obfuscation
In the realm of app development, the specter of reverse engineering looms large. Malicious actors can effortlessly extract sensitive information if your code isn’t fortified. Enter code obfuscation a potent technique that obliterates the readability of your code. Code obfuscation obscures functions and class names within compiled Dart code, perplexing potential hackers. By wielding the `-obfuscate` parameter from the Dart side, you can cloak your data and fortify your Flutter app against prying eyes.
Code obfuscation can be enabled in your Flutter project through the build settings. The following should be added to your build.yaml file in pubspec.yaml:

[Fig:1 Code Obfuscation Configuration]
By employing this method, you’ll make it more challenging for reverse engineers to comprehend your main.dart file.
Secure API Keys
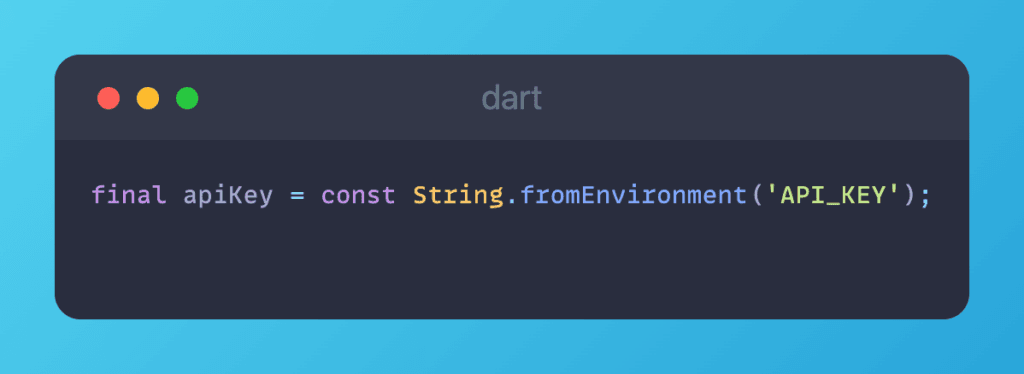
API keys serve as the gatekeepers between your app and back-end services. However, if they’re not properly safeguarded, they can transform into Achilles’ heels. Implement application restriction controls to stipulate which applications, websites, or IP addresses can access your API keys. Enhance security by encrypting and decrypting API keys on the fly, thwarting hackers’ decryption attempts. Never store API keys in your repository a cardinal sin that can lead to unwelcome exposure. Remember, Firebase Remote Config isn’t the bastion for safeguarding sensitive data due to its inherent limitations.
You should use environment variables or a configuration file to store API keys securely when working with APIs. Hardcoding keys directly into your code is not a recommended practice. For instance:
[Fig:2 Secure API Key Usage]
It is recommended that the API_KEY environment variable is set during deployment in order to protect it.
Flutter_jailbreak_detection
Devices subjected to jailbreaking or rooting pose a menacing security threat. They grant users unwarranted privileges, creating a welcome mat for malware and app infiltration. To combat this threat, Flutter offers the flutter_jailbreak_detection package, a sentinel that detects whether your app is running on compromised devices. Harnessing this package empowers your Flutter app to deploy RootBeer on Android and DTTJailbreakDetection on iOS, instating a digital moat against potential security breaches.
Implement jailbreak/root detection using flutter_jailbreak_detection :

[Fig:3 Jailbreak Detection]
Ensure Secure Network Connections
Creating secure network connections acts as a sentinel guarding the gates of data security. Embrace the power of Transport Layer Security (TLS) to forge impervious channels between your mobile app and servers. Bolster security by whitelisting your domain to quell unruly traffic. Seal the deal with certificate pinning a formidable defense mechanism that thwarts hackers’ tampering endeavors using forged certificates.
Implement secure network connections using HTTPS and the http package:

[Fig:4 Secure Network Connection]
Use Only Necessary Permissions
Mobile applications often cast wide nets, soliciting permissions that extend beyond necessity. Reduce excess by avoiding plugins that request unnecessary permissions. Adhere to the principle of least privilege grant permissions sparingly, and revisit them regularly.
When seeking permissions, be selective and request only those that are genuinely necessary for your app’s functionality. For instance, if your app doesn’t require access to the user’s location, refrain from requesting location permission
Secure User Data
Sometimes, your app holds the crown jewels: sensitive data like Personally Identifiable Information (PII) and authentication tokens. To shield this treasure trove, enlist the aid of the flutter_secure_storage package, which calls upon Android’s Keystore and iOS’s Keychains. For additional reinforcement, consider using Hive, a Dart package that serves as a steadfast guardian, thwarting tampering attempts.
Employ the flutter_secure_storage package for the secure storage of sensitive data, such as authentication tokens

[Fig:5 Securely Storing User Authentication Token]
Background Snapshot Protection
Mobile devices often flaunt snapshots of apps in their task-switcher, inadvertently revealing sensitive information. The remedy? The secure_application package is a cloak that shrouds your app’s content in secrecy, even when it lurks in the shadows.
Employ the secure_application package to hide your application’s content when it goes into the background, ensuring the protection of sensitive information from exposure in snapshots.
Implement Local Authentication:
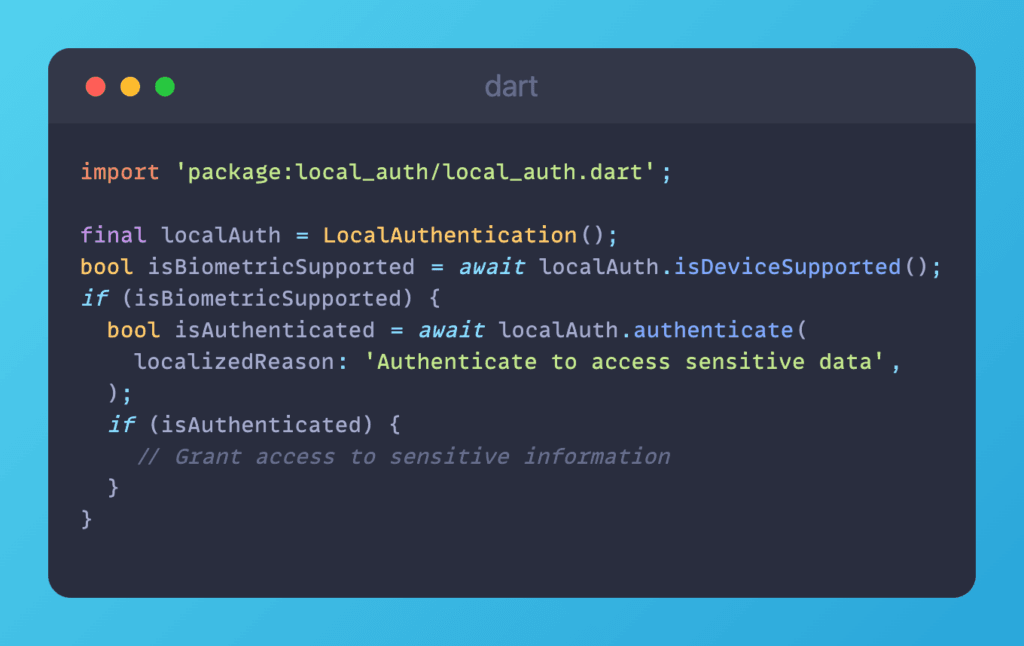
For apps entrusted with treasure chests of sensitive information like payment details, local authentication is the trump card. The local_auth Flutter plugin steps onto the scene, wielding the power of biometric authentication. This additional layer of protection ensures that only authorized users can access the fortress, especially in cases of lost or stolen devices.
Implement local biometric authentication using the local_auth package.
[Fig:6 Implementing Local Biometric Authentication]
Secure Developer Identity
Developer identity and sensitive files hold the keys to the kingdom. Protect them through encryption encase files like key.jks and keystore.properties with GPG (GNU Privacy Guard). Whatever you do, never lay bare unencrypted sensitive data in your repository.
Securing developer identity and sensitive files is of paramount importance. Employ encryption, such as GPG (GNU Privacy Guard), to safeguard critical files like ‘key.jks’ and ‘keystore.properties.’ Never expose unencrypted sensitive data within your repository.
Secure CI Infrastructure
In the realm of Continuous Integration (CI), vigilance reigns supreme. Regularly scan for vulnerabilities, and keep virtual machines fortified with the latest defenses. Guard secrets, such as API keys, zealously never expose them in your code. Instead, lock them securely in your project’s secret vault.
Within your Continuous Integration and Continuous Deployment (CI/CD) pipeline, it’s crucial to give priority to securing sensitive information like API keys. Instead of hardcoding these credentials directly into your code, best practice dictates that you securely store them as environment variables. Additionally, consider incorporating security scanning tools into your CI infrastructure to proactively detect and address vulnerabilities.
Additional Security Best Practices
To consistently safeguard your Flutter applications for the uncharted territories of 2023 and beyond, keep these overarching best practices in mind.

[Fig:6 Additional Security Best Practices]
- Stay Informed with the Latest Updates
- To keep your Flutter apps safe in the evolving landscape of 2023 and beyond, it’s essential to stay up-to-date.
- Stay informed by regularly checking for the latest releases, plugins, and packages within the Flutter SDK.
- These updates often bring crucial security enhancements that protect your applications.
- Manage Dependencies Wisely
- Building your app’s foundation requires careful selection and vigilant maintenance of dependencies.
- Avoid the temptation to fixate on specific versions, as this can expose you to security risks.
- Periodically review your dependencies and align them with the most recent offerings to bolster your app’s security.
- Keep Your Flutter Version Current
- If you’ve customized your Flutter environment, it’s vital to ensure it’s always in sync with the official releases.
- Custom versions may lag behind in vital security fixes.
- Stay secure by promptly updating your Flutter to the latest version, so you have the most robust defenses at your disposal.
Conclusion
In an era where data breaches and security threats are on the rise, safeguarding your Flutter applications is paramount. By adhering to these data security best practices in 2023, you can strengthen your apps against potential threats and guarantee the safeguarding of sensitive information. Keep your technologies up-to-date, stay vigilant, and prioritize the safety of your users’ data.
 Healthcare
Healthcare  Education
Education  Real Estate
Real Estate  Logistic
Logistic  Themes
Themes
 Plugins
Plugins
 Patterns
Patterns